Two critical zero-day security vulnerabilities — CVE-2023-37265 and CVE-2023-37266 — have been unearthed in CasaOS, allowing a threat actor to bypass authentication requirements and gain full access to the CasaOS dashboard.
Cybersecurity researchers from SonarSource analysed the two vulnerabilities in detail. The situation is even more alarming because the public release of these vulnerabilities occurred shortly after the vendor addressed them, potentially leaving unpatched instances at risk.
CVE-2023-37265
The first vulnerability, CVE-2023-37265, allows an attacker to bypass authentication requirements. This provides malicious actors with unrestricted access to the data stored on the device, and it can be used as a springboard to launch further attacks into internal networks.
CasaOS is not a lone software but a set of services that operate on top of a distribution like Ubuntu or Debian.
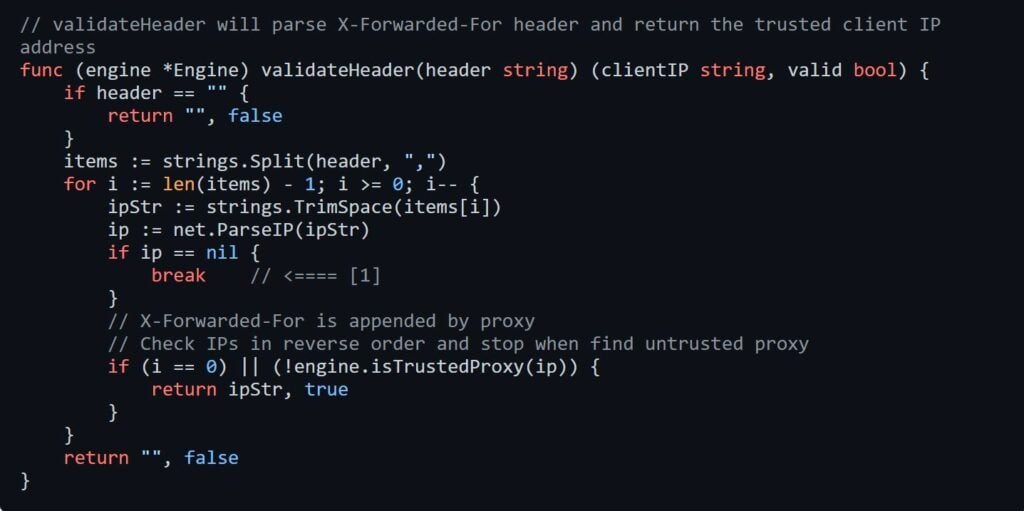
The first component to receive user requests is casaos-gateway, the only service directly exposed to the network. It forwards requests to various local microservices based on the request path. While many services only listen on localhost, casaos-gateway forwards requests to these services as needed.
However, one common problem with reverse proxies like casaos-gateway is that the final service sees all requests as originating from the reverse proxy itself, with the source IP address at the network layer level always being localhost. To address this issue, the reverse proxy typically uses the X-Forwarded-For header to relay the client’s real IP address to the application.
In this case, CasaOS has always used casaos-gateway as the reverse proxy, so there’s no inherent issue. However, some applications may mistakenly trust this header without verifying the presence of a reverse proxy, potentially exposing vulnerabilities like CVE-2023-37265.
CVE-2023-37266

While investigating the first vulnerability, researchers observed an unusual behaviour related to the session JSON Web Tokens (JWT). When the researchers modified the token’s claims and signature, it did not result in errors signifying that something was likely wrong.
Further analysis revealed that CasaOS used an empty HMAC-SHA256 secret for JWT verification, making it vulnerable to arbitrary JWT creation.
An attacker could exploit this vulnerability to craft valid-looking but unsigned tokens, bypassing authentication and gaining administrative privileges on vulnerable CasaOS instances.
When the researchers disclosed the vulnerabilities to CasaOS, the developers released CasaOs v0.4.4 to patch them, make changes to the outgoing X-Forwarded-For headers, and ensure token signature validation.
In the News: Actively exploited Cisco zero-day affects potentially 80000 devices






