A new Chinese state-backed cyber espionage campaign has been discovered that targeted organisations in other countries, especially in Taiwan. This discovery has raised alarms due to its potential for wider global impact.
Microsoft recently exposed a campaign by a group named Flax Typhoon, originating from China and aimed at its arch-nemesis, Taiwan. The threat actor shares attributes with another actor, Ethereal Panda. Microsoft’s threat intelligence has unveiled Flax Typhoon’s strategies, suggesting a focus on prolonged access and covert reconnaissance within victim organisations across diverse sectors. Despite its aggressive intentions, Microsoft observes that Flax Typhoon has yet to execute its final objectives.
Flax Typhoon’s modus operandi employs various tactics, including exploiting known vulnerabilities in publicly accessible servers to gain a foothold. The campaign capitalises on ‘living-off-the-land’ techniques, using legitimate tools already available on the target system, rendering detection and prevention intricate. Notably, compromised accounts and ‘LOLBins’ (living-off-the-land binaries) play crucial roles in its strategy, making response even more complex.
The campaign’s targets extend beyond Taiwan, encompassing regions like Southeast Asia, North America, and Africa. Organisations in government, education, critical manufacturing, and information technology sectors have all fallen victim to Flax Typhoon’s persistent attacks. This geographical diversity emphasises the campaign’s global reach and potential consequences.
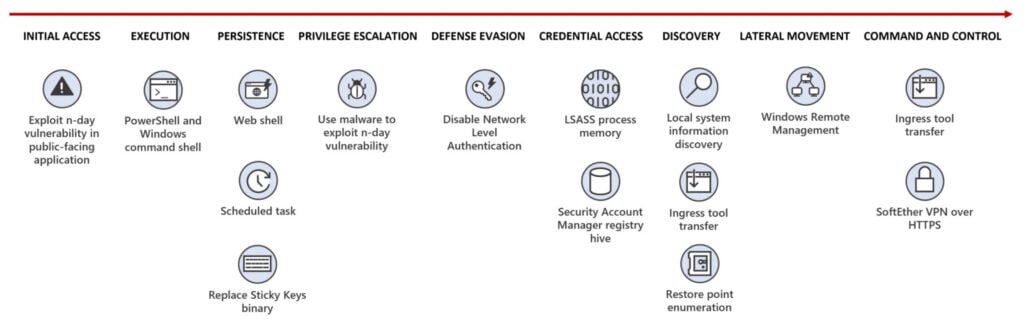
Flax Typhoon’s toolkit compromises tools like China Chopper web shell, Metasploit, Juicy Potato privilege escalation tool, Mimikatz, and SoftEther VPN client. The attackers adeptly manipulate these tools alongside living-off-the-land techniques, which are challenging to counter. For instance, the group gains initial access through web shells and leverages legitimate utilities to secure lasting entry through the remote desktop protocol (RDP).
The initial breach occurs through the exploitation of vulnerabilities in public servers. This is followed by the group establishing a VPN connection to amass credentials from compromised systems. This access enables them to scour systems for additional vulnerabilities, and their choice of reputable VPN tools contributes to disguising the connection’s malicious nature. Microsoft explained that this traffic closely resembles genuine HTTPS activity, a characteristic that often eludes detection by common network security appliances, making it difficult to intercept.
Microsoft advises organisations to bolster their defences against such attacks. Vital steps include maintaining updated public-facing servers, enforcing robust patch management, enabling strong multifactor authentication (MFA), and undertaking network monitoring to identify suspicious activities.
Chinese threat actors have been known to target countries like Taiwan, India, and the autonomous region of Hong Kong. China aims to attain a global superpower status and will go to any lengths to achieve it.
In the News: AI chatbots are assisting content farms in plagiarising news articles






