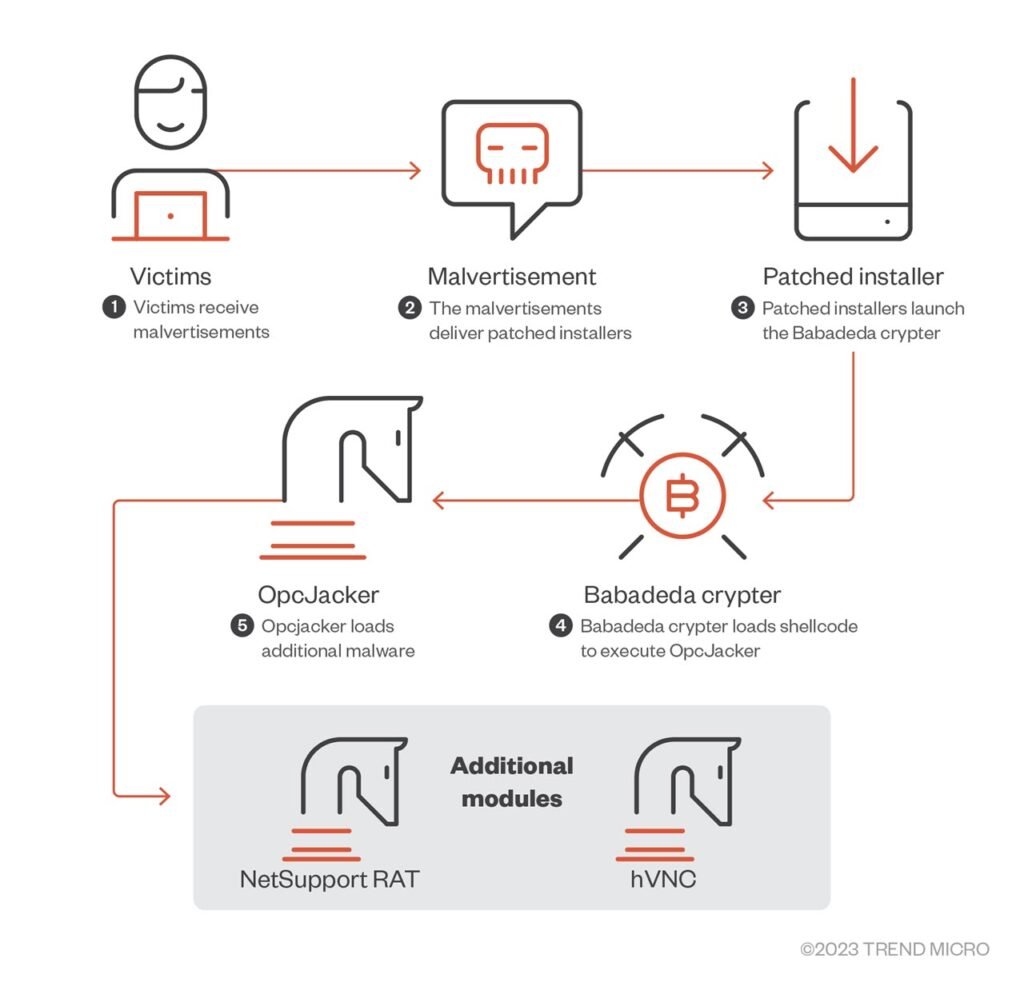
Security researchers have discovered a new malware dubbed Opcjacker because of its opcode configuration design and cryptocurrency-hijacking abilities. The malware has been distributed in the wild at least mid-2022 using malvertising campaigns disguised as cryptocurrency applications and other legitimate software distributed via fake websites.
In its latest February 2023 campaign discovered by Trend Micro researchers, the malware was being distributed by a malvertising campaign geofenced to users in Iran. The malvertisements themselves were disguised as a legitimate VPN app tricking the users into downloading an archive file containing Opcjacker.
The Trend Micro report claims that Opcjacker is “an interesting piece of malware” because its configuration uses a custom file format to define the stealer’s behaviour. The format resembles custom virtual machine code which has numeric hexadecimal identifiers in the configuration file controller the malware’s behaviour and running whatever functions the threat actor desires. This is likely done to confuse researchers working on analysing and understanding the malware.
Overall, Opcjacker’s capabilities include:
- Keylogging
- Taking screenshots
- Stealing sensitive browser data
- Loading/delivering additional modules and payloads
- Replacing copied crypto addressed in the clipboard for hijacking
The malware loads itself by patching a legitimate DLL library inside an installed program which then loads another malicious DLL library which finally assembles and runs the shellcode containing the loader and runner of another malicious application in addition to Opcjacker, which is assembled from chunks of data stored in multiple files of different formats such as WAV and CHM.
This malware loader has been used for over a year and is called the Babadeda crypter. That said, the threat actor behind Opcjacker did make some changes to the cryptor in addition to adding a completely new payload.

Additional modules dropped by Opcjacker include either the NetSupport RAT or a hidden VNC variant. Researchers also found reports of another loader called Phobos Cryptor which is the same malware as Opcjacker being used to load the Phobos ransomware.
The main purpose of the malware isn’t known yet, but its crypto-stealing abilities indicate that it may be financially motivated. That said, additional functions in the malware also allow it to be used as an info stealer and malware loader, meaning it can be used for a number of malicious purposes. The campaign IDs found in the samples that researchers analysed suggest that Opcjacker is still under active development, which means we could see wider adoption within threat actors and its use in other malicious campaigns.
In the News: Elon Musk and others urge to suspend AI development past GPT-4






