As many as 50 Wordpress sites are using a plugin called Fuser-Master that uses popunder traffic to promote these websites. The plugin mimics human behaviour by automatically scrolling a page and following links mentioned on the page using a specialised URL that the plugin itself creates. Several ads from different providers are loaded and refreshed during this behaviour.
According to the Malwarebytes report on the plugin, one of the blogs using this ad fraud had 3.8 million visits in January 2023, with reportedly 17.50 pages per visit and 24:55 minutes of visit duration. The plugin, allegedly developed by an undisclosed Indian web developer, loads sites on a page underneath the one visited by the user to display several ads while also monitoring the user’s cursor to stop the fake scrolling as soon as the cursor is taken away from the site’s viewport.
The researchers weren’t able to find many mentions of the plugin, with all the information coming from themesinfo.com, a Wordpress theme detector that shows the name of the plugin and some sites that currently use it to run the fraud.
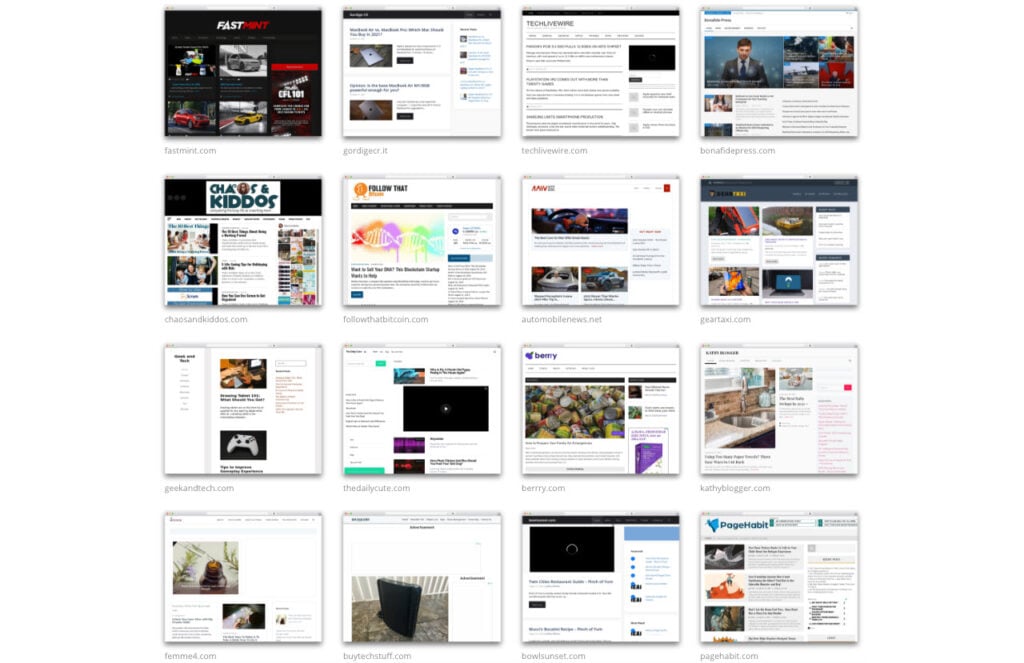
It’s also worth pointing out that these sites aren’t automatically fraudulent by nature. The blogs and static until the user visits a specific URL entry point generated by the plugin, which then prompts the zombie activity. The plugin first performs a check to determine whether or not they should be allowed to enter the ad fraud scheme or not.
Once a user is flagged safe, the popunder loads the blog via the generated entry point and immediately leaves it to re-enter via a Google open redirect, much like a real user. Since the blog opens in a window behind the current window, the user is unaware of what’s happening.
Once a blog is opened, it’s randomly scrolled up and down, and a new article is opened at regular intervals. This fake activity can continue for minutes to hours until the real user interrupts and closes the popunder window. If the user closes the window in front of the popunder, all fake activity stops, and the blog becomes static.
The Malwarebytes team reached out to one of the customer sites running this plugin. While they did not hear back from the customer itself, the plugin was disabled on the site within an hour of communication.

While popunders aren’t exactly malicious and are, in fact, a legitimate form of advertising, their format can be easily abused to create frauds like these, where websites are automatically loaded and scrolled with open ads that are unlikely to be seen by a real human.
The fuse-master plugin abuses this to significantly increase a blog’s earnings while keeping the blog from being flagged by anti-ad fraud platforms. All that’s required to run the fraud is purchased ad space via a popunder distributed and the special entry point URL to trigger the plugin.
In the News: M1 and M2 Macs can now officially run Windows 11 via Parallels






