Cybersecurity researchers at ReasonLabs have uncovered a massive multi-million dollar scam operation that has been extracting millions out of credit cards since at least 2019, with the victim count in the tens of thousands.
The operation is essentially a network of fake dating and customer support websites that are used to charge credit cards bought on the dark web. ReasonLabs believes that the operators come from a Russian crime syndicate.
Several security companies, including McAfee and ReasonLabs itself, have been abused for these fake charges. The entire infrastructure is built on Amazon Web Services and uses GoDaddy to circulate its over 275 domains. Candid.Technology tested 50 of the 275 domains listed in ReasonLabs’ report randomly, and all sites remain online at the time of writing.
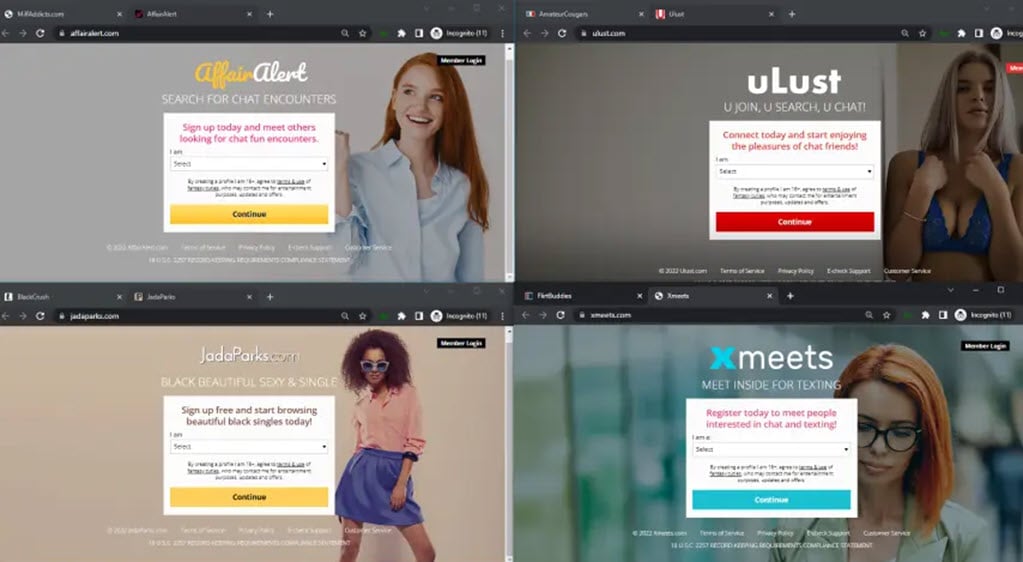
To avoid being blacklisted by payment acquirers, each website applied individually to prevent the whole operation from collapsing should a single site gets rejected or the operation is discovered. As proof of legitimacy, all the sites have a 24/7 support chat feature and a working telephone line handled by an outsourced support centre provider.
All sites also feature a toll-free number for subscribers to cancel their payments to add another layer of legitimacy not usually seen in scam sites. Once the payment processor approves, the operators dump credit cards found on the dark web and charge them on the sites to extract money.
Most of the victims of the operation are from the US, as the sites themselves are registered there. That said, considering some sites in the operation are in French, it can be assumed that at least some of the customers belong to French-speaking countries.

To avoid detection, the operators used small recurring payments with amounts similar to other subscription services and refrained from performing any test transactions before the main charge.
To further stay under the chargeback rate that most payment processors apply, the operations used generic names, ensuring consumers didn’t know what the charge is about in addition to implementing the aforementioned layers of legitimacy.
ReasonLabs has reported the network to over a dozen parties involved, including Visa, Mastercard, AWS, GoDaddy and other involved registrars, as well as law enforcement and Fraud.org, part of the U.S National Consumer League, a nonprofit advocacy organisation in the US which reports consumer complaints to a network of over 200 law enforcement agencies.
In the News: Optus breach exposes customer data; Services remain unaffected






