Apple CPUs are vulnerable to GoFetch attack, a sophisticated microarchitectural side-channel exploit that targets data memory-dependent prefetchers (DMPs) in Apple’s silicon, namely the M1 and M2.
This attack method poses a significant threat to cryptographic implementations that rely on constant-time programming paradigms, allowing malicious actors to extract secret keys from vulnerable systems.
A team of researchers from various universities detailed the GoFetch attack, which leverages the inherent behaviour of DMPs found in Apple m-series CPUs. These prefetchers, designed to predict and fetch data from memory, tend to activate and attempt to dereference data resembling points.
The researchers disclosed the findings to Apple on December 5, 2023, 107 days before the public reveal.
This behaviour directly contradicts the principles of constant-time programming, which demand uniform execution times for all operations irrespective of data or memory access patterns.
To execute the GoFetch attack, threat actors craft specific inputs to cryptographic operations, strategically introducing pointer-like values that only manifest if certain bits of the secret key are correctly guessed. Through careful analysis and cache-timing techniques, attackers can verify these guesses and progressively extract key bits from implementations such as OpenSSL Diffe-Hellman, Go RSA, CRYSTALS Kyber, and Dilithium.
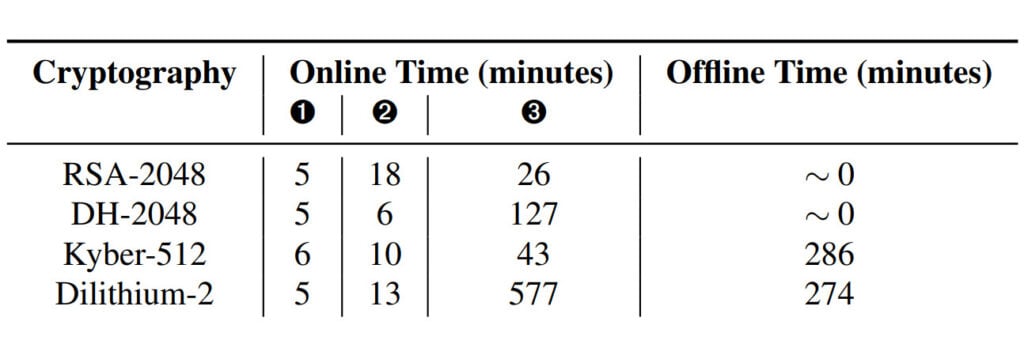
One of the key revelations from this research is the widespread presence of DMPs across Apple’s CPU lineup. The attack has been successfully demonstrated on m1 processors, and while not directly tested on other variants like m2 and m3, the shared microarchitecture suggests a similar vulnerability.
Additionally, Intel’s 13th-generation Raptor Lake microarchitecture features a DMP, albeit with more restrictive activation criteria that mitigate some attack vectors.
The researchers highlighted a crucial distinction between GoFetch and the previously discovered Augury exploit. While Auguary initially identified the potential for DMPs to mix data and addresses, GoFetech demonstrates significantly more aggressive DMP behaviour, amplifying the security risk posed by these prefetchers.
Constant-time programming, a cornerstone in defending against side-channel attacks, faces a new challenge with the emergence of DMP-based exploits. Despite efforts to adhere to constant-time principles, the GoFetch attack illustrates how DMPs can generate secret-dependent memory accesses, compromising the integrity of cryptographic implementations.
In response to these findings, researchers have recommended user and developer steps. Users are advised to update their software regularly, while developers can explore options like disabling DMPs on compatible processors or implementing input blinding techniques to mitigate vulnerabilities.
In the News: GitHub launches Code Scanning Autofix in public beta






