Researchers from ESET have exposed a Mustang Panda campaign taking advantage of Russia’s invasion of Ukraine to spread a new Korplug malware.
This new version, called Hodur, is being spread through a phishing campaign taking advantage of multiple topics of interest in Europe, including the currently ongoing Ukraine crisis. The campaign has adapted to different events since August 2021 and is still ongoing.
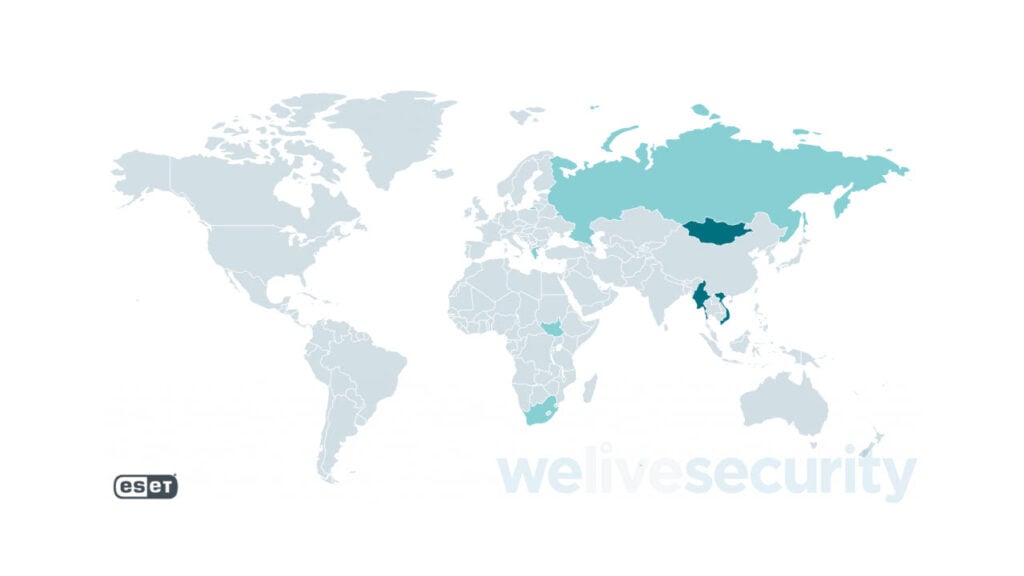
Using this strategy, Mustang Panda has infiltrated multiple research organisations, ISPs and systems belonging to European diplomats across countries, including Cyprus, Greece, Mongolia, Myanmar, Russia, South Africa and Vietnam.
In the News: Lapsus$ hacking group is run by a UK-based teenager
Benefitting from the war
Korplug was previously used in attacks against the Afghanistan and Tajikistan militaries as well as multiple other high-value organisations in Russia and a few targets in Asia. According to the researchers, Chinese threat actors have used variants of the trojan since at least 2012.
The new variant is similar to Thor, another variant of the malware detected by Palo Alto Networks in 2021 deployed during the Microsoft Exchange server incident.
ESET is not currently sure of the campaign’s source yet, but these phishing and watering hole attacks are likely meant to gain initial access. Downloaders for Hodur have been found in decoy documents with names including:
- COVID-19 travel restrictions EU reviews list of third countries.exe
- State_aid__Commission_approves_2022-2027_regional_aid_map_for_Greece.exe
- REGULATION OF THE EUROPEAN PARLIAMENT AND OF THE COUNCIL.exe
- Situation at the EU borders with Ukraine.exe

These executable files open a document with the same name but with either a .doc or .pdf extension. The file contents align with the title, with at least one of them being a publicly accessible legitimate document for the European Parliament.
Upon execution, the file downloads a decoy document, a legitimate executable file, a malicious module and an encrypted Korplug file. The last three components execute a payload via DLL-sideloading, which Mustang Panda uses. Once everything is downloaded, the decoy document is launched to distract the user while the payload launches itself silently in the background.
In the News: Cybercrime victims lost over $6.9 billion in 2021: FBI






