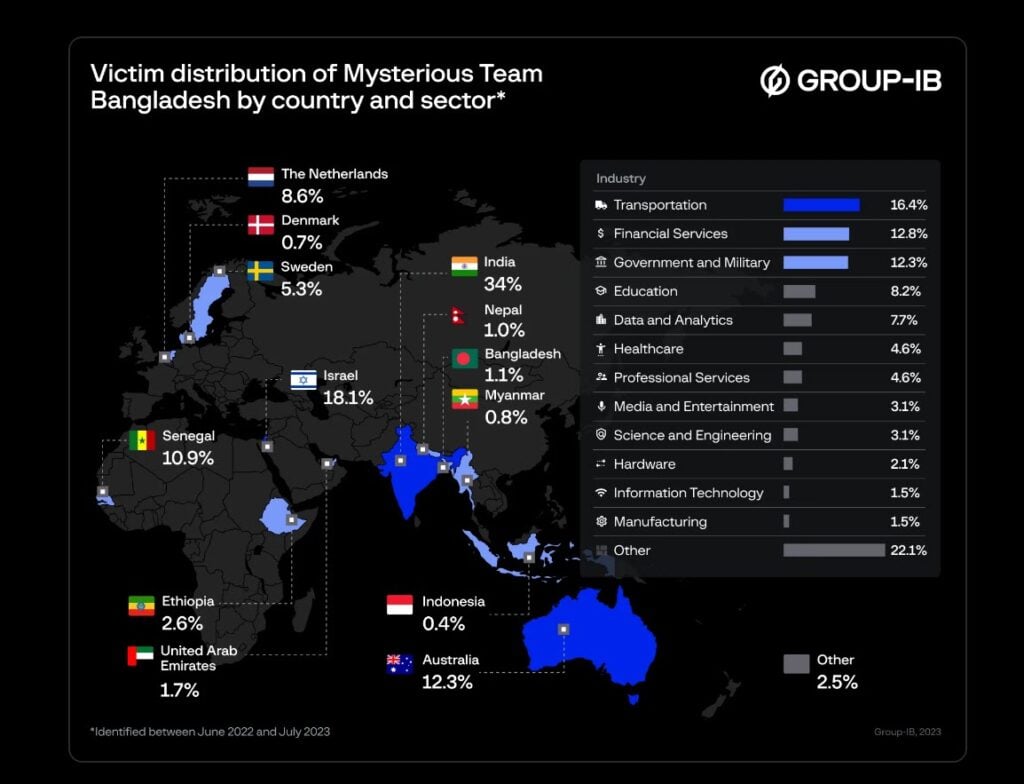
A cybercriminal group Mysterious Team Bangladesh has carried out a total of 846 DDoS attacks in the past year out of which over 750 were targeted towards Indian entities. Other countries include Israel, Australia, Senegal, and Sweden, among others.
The group emerged in 2020 but remained relatively obscure until 2022. Their activities have since escalated, with an increasing number of Distributed Denial of Service (DDoS) attacks and website defacements targeted at governments, and financial, and transportation sector organisations.
According to a report by the Group-IB Threat Intelligence Unit, Mysterious Team Bangladesh has been highly focused on Inda, carrying out over 750 DDoS attacks and 78 website defacements since June 2022. The group is believed to have gained unauthorised access to web servers and administrative panels using known vulnerabilities and common/default passwords for admin accounts.
The origins of Mysterious Team Bangladesh can be traced back to a threat actor D4RK TSN, as documented on the group’s EverybodyWiki page, which was created in 2022. While some suggest the group was formed in 2020, there is limited evidence of any activity until 2022. This has led experts to speculate that the group might have operated under a different name before rebranding.
This politically and religiously motivated gang follows a pattern of launching thematic campaigns triggered by specific news events, focusing on particular countries for short periods before reverting to their main targets: India and Israel. They predominantly target government resources, banks, and financial organisations, but also exploit domains within a country’s domain zone if specific targets are not readily available.
Group-IB’s analysis reveals that Mysterious Team Bangladesh prefers to attack victims using widely deployed and outdated services, such as PHPMyAdmin and WordPress, exploiting known vulnerabilities in these frameworks. The group employs various open-source utilities like Raven-Storm, Xerxes, and Hulk to execute DDoS attacks at different network layers, including Layer 3, Layer 4, and Layer 7.
The group is not acting alone, and its Telegram channel suggests it is affiliated with other collectives, including Khalifah Cyber Crew, AnonGhost, DragonForce Malaysia, and Ghosts of Palestine, among others.

As of July 2023, Mysterious Team Bangladesh remains highly active and has expanded its attacks to target countries such as Senegal, Ethiopia, Australia, Sweden, the Netherlands, and more. Experts predict the group will continue to intensify its attacks in Europe, Asia-Pacific, and the Middle East, focusing on financial companies and government entities.
To mitigate the risk posed by Mysterious Team Bangladesh, organisations are advised to deploy load balancers, configure firewalls and routers to filter suspicious traffic, and use content delivery networks (CDN) for traffic distribution. Regularly updating web-server backend software and leveraging threat intelligence solutions and also enhance risk mitigation efforts.
In the News: Amazon Web Services face RAT exploitation from own SSM Agent






