Remcos Remote Access Trojan (RAT) malware, disguised as adult games and distributed through webhard platforms, has been circulating in South Korea.
Webhards are remote file-hosting services that make it quite easier to download and upload illegal data, including films, video games, and porn. These platforms are also a go-to spot for threat actors to distribute RATs. Earlier, webhards were used to disseminate malware like UDP RAT and njRAT, camouflaging as legitimate files.
Cybersecurity researchers from AhnLab Security Intelligence Center (ASEC) discovered that a third malware, RemcosRAT, is also being distributed via the same platform.
Researchers found that the malware was strategically concealed within various games, utilising a common method. According to ASEC, these deceptive games often come with a guide instructing users to run the Game.exe file that users may find seemingly innocuous game launcher files.
However, ASEC’s investigation revealed that the actual dynamic-link library (DLL) responsible for running various games exists separately. Malicious Visual Basic Scripts (VBS) are executed alongside the game file when users run Game.exe.
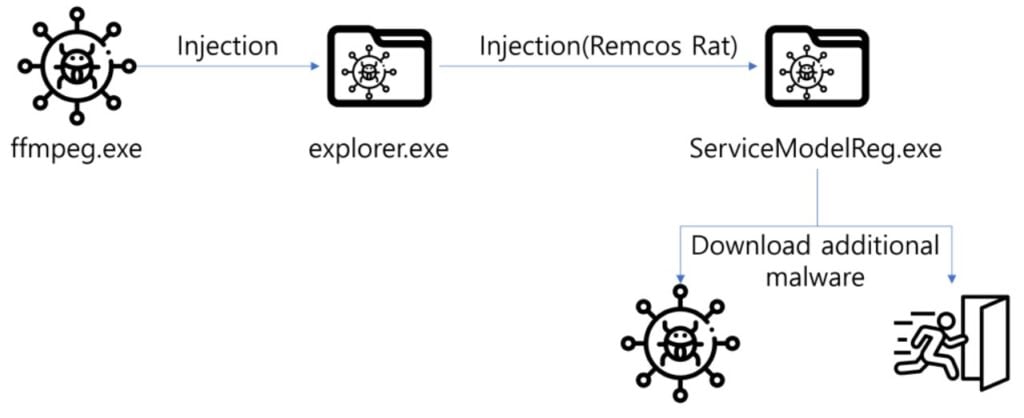
The ultimate execution involves the ffmpeg.exe malware. Upon execution, the malware splits the ‘sexyz’ string to extract the encrypted binary and Key value from test.jpg. These extracted elements are then injected into explorer.exe.
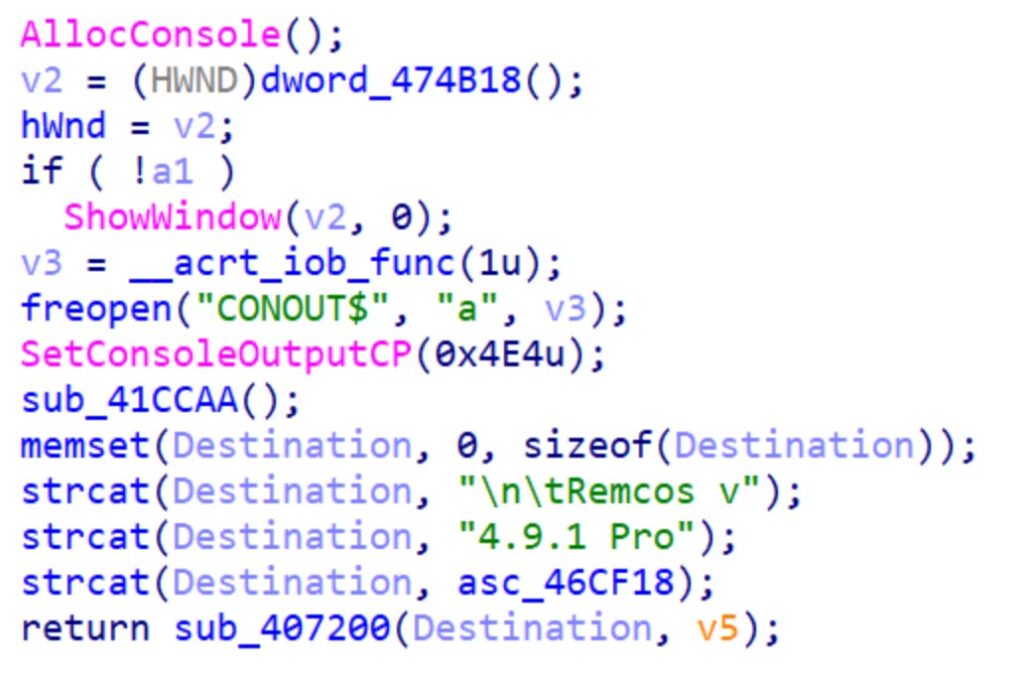
The injected malware downloads the RemcosRAT through the command and control (C&C) server. Additional malicious activities are attempted by injecting the RAT into ServiceModelReg.exe.
“Users need to take caution as malware is being distributed actively via file-sharing websites such as Korean webhards. As such, caution is advised when running executables downloaded from a file-sharing website. It is recommended that users download programs from the official websites,” urged the researchers.
In August last year, threat actors combined TargetCompany ransomware and RemcosRAT, employing fully undetectable (FUC) packers and adding a layer of sophisticated obfuscation to the payloads.
In the News: Real money games get Google’s support in India, Mexico and Brazil






