If common spyware apps like Pegasus weren’t a big enough headache for government critics, journalists and human rights activists, there’s a new threat that is much more likely to affect the average person. According to Jack Whittaker’s TechCrunch report, there’s an entire fleet of Android spyware apps that are exposing everyday people’s phone data, and they all share the same vulnerability.
This fleet of apps was first discovered as part of a wider investigation into consumer-grade spyware apps. At the moment, this spyware operation has about 400,000 victims around the world, including countries like the US, Brazil, India, Indonesia, Jamaica, South Africa, Russia and the Philippines.
If that isn’t alarming enough, the vulnerability mentioned above in these apps allows an unknown attacker to access data streams from any of the devices these spyware apps have access to without much of a hassle. Given the scale of the operation and the complexity of informing the victims, the vulnerability disclosure centre at Carnegie Mellon University’s Software Engineering Institute, CERT/CC, has issued a note as well.
Here’s a summary of what’s going on with this massive operation.
- There are a total of nine apps found part of the fleet — Copy9, MxSpy, TheTruthSpy, iSpyoo, SecondClone, TheSpyApp, ExactSpy, FoneTracker and GuestSpy.
- The apps are nearly identical in nature with some even having the same user interface for setting up the app.
- Once planted, the apps give a remote operator a web dashboard from where they can access the victim’s phone data in real time including but not limited to messages, contacts, location and photos.
- In a similar fashion to the apps, the dashboards are also pretty much clones of each other.
- All nine apps contact the same server infrastructure. The infrastructure seems to be controlled by a Vietnam-based tech company called 1Byte.
- App apps suffer from the same vulnerability, called IDOR or Insecure Direct Object Reference. It’s a class of bug that exposes files or data on a server because of poor or no security measures in place.
- An authenticated remote attacker with access to one of the stalkerware variants can acess personal information from any device targeted by either of the apps.
- The operator, 1Byte, can address this vulnerability, but hasn’t responded to any communication regarding the vulnerability.
- At the moment, there are 400,000 devices across the world impacted by these apps. The actual number might be higher as targets grow daily.
You can read TechCrunch's report for more information on the apps, the operators and their modus operandi here.
In the News: OpenSea phishing scam: $1.7 million worth of NFTs lost
How to protect yourself against Spyware?
If you believe these stalking apps are targeting your device, here are some steps you can take to protect yourself. Keep in mind that removing such apps will inform the operator, which can cause a dangerous situation.
Change your phone password
The first thing you should do in such situations is change your phone’s password. If a stalkerware app was installed on your phone, chances are your lock screen password, pin, or pattern was either guessed, hacked or learned. Changing it is the first step to securing your device.
Uninstall unrecognised apps
Most malware or spyware apps will disguise themselves as a system process and hide their icons from the UI launcher. However, they appear in the apps list under your device’s settings. Check to make sure you don’t have any unrecognised apps in there, and if you do, you might want to remove them.

- Head over to your phone’s settings and tap Apps.
- Tap Show all apps.
- Find and delete any unrecognised apps in the list,
Check your Google Play Protect settings
Google’s Play Protect is one of the best and simplest ways to keep your phone safe from malicious apps. However, this can be disabled and can leave your phone vulnerable. Check to ensure that Google Play Protect is enabled and that your phone has recently been scanned.

- Open the Google Play Store and tap on your profile picture in the top-right.
- Tap Play Protect.
- Make sure that it’s enabled and a recent scan was completed. You can also scan your phone by tapping the Scan button.
Check your accessibility settings
Spyware apps often abuse Android accessibility settings, which by design have a deeper level of access to your phone’s OS and data for its features to work. If you don’t see a downloaded or recognisable app in your accessibility services list, there’s a chance it might be a stalkerware app in disguise.
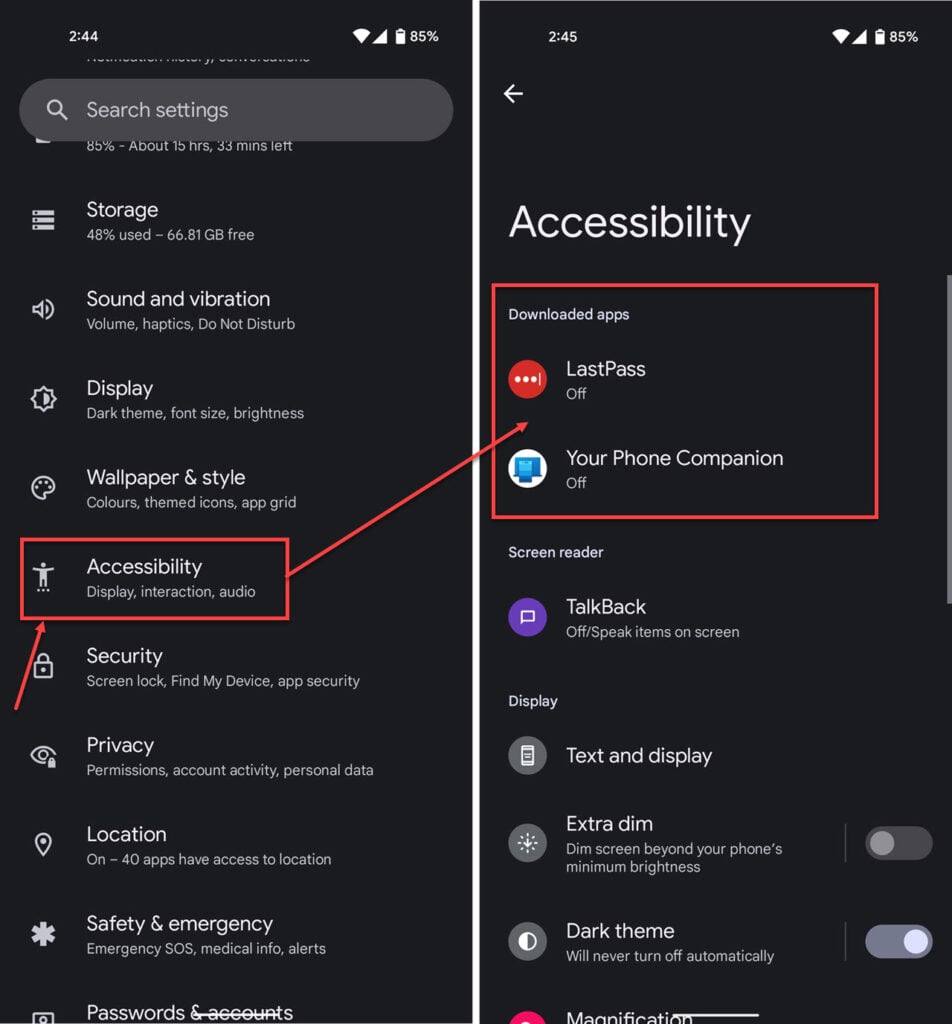
- Head over to your phone’s settings and tap Accessibility.
- Check to make sure there aren’t any unknown apps using accessibility features on your phone.
Check for any device administrator apps
Device admin apps are helpful for companies to remotely manage their employee’s phones, wipe data to prevent data loss and manage features. However, these apps’ permissions can also allow stalkerware to snoop on users.
Check to see if there are any unrecognised device admin apps on your phone and if there are, remove them immediately.

- Head over to your phone’s settings and tap Apps.
- Scroll down and tap on Special app access.

- Tap Device admin apps
- Make sure no malicious or unrecognised apps are allowed admin permissions.
Factory reset your device
The last resort and possibly the safest option to remove any malware or spyware hidden deep inside your phone is to factory reset your device. This will cause you to lose all data you haven’t backed up, but at the same time, it’ll also get rid of everything that didn’t come installed with your phone, which includes the stalkerware apps.
We did a video demonstrating how such spyware can get onto your phone and track your data and location. Check it out below.
In the News: IRS rolls out a temporary authentication system following biometric row







