Ukraine’s Computer Emergency Response Team (CERT-UA) reports having stopped an attack on an energy facility in the country with help from ESET and Microsoft. The attack was launched by Sandworm, a hacking group known to work with Russian military intelligence.
CERT reported the objective of the attack was to destroy high-voltage electrical substations and compromise Windows computers, network equipment and servers running Linux at the facility. The group also discovered a new version of the Industroyer malware, which was used to disrupt power in Ukraine, leaving hundreds of thousands of people without power two days before Christmas back in 2016.
Researchers at cybersecurity firm ESET who worked with CERT to analyse and defend against the attack, have assessed with high confidence that the malware used in the attack was built using the source code of the same Industroyer malware deployed in 2016. This new version has been named Industroyer2 by the researchers.
In the News: T-Mobile paid a $200,000 ransom to hackers; still, the data was leaked
Defending Ukraine’s critical infrastructure
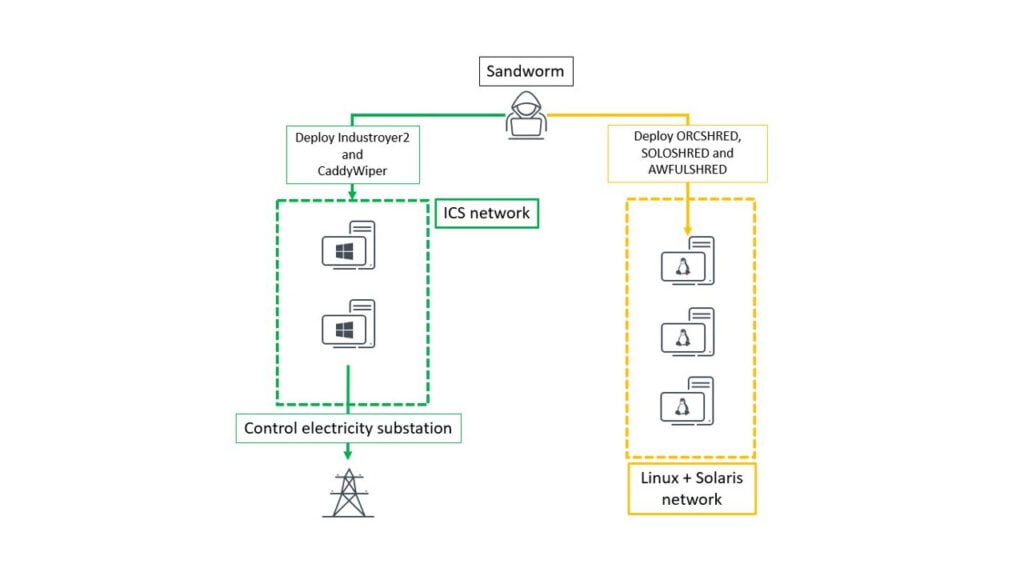
ESET’s report notes that there were several other malware families that targeted different parts of the energy substation.
- Industroyer2 was used to target the main high voltage electrical substations.
- Computers running Windows at the facility were targeted using the CaddyWiper malware and the ArguePatch loader.
- Linux servers at the facility were targeted using the Orcshred, Soloshred and Awfulshred script-destructors.
CERT’s advisory states that the attackers gained access to the energy provider’s network no later than February 2022 and had scheduled a shutdown of the electrical substations and the failure of the facility’s infrastructure on April 8. The implementation of Sandworm’s plans has so far been prevented.
This new campaign is the latest in a series of attacks targeting different sectors in Ukraine. At the moment, ESET doesn’t know how the attackers compromised the network or how they moved from the IT network to the ICS network.
In the News: Cybercriminal hub, Raidforums, goes offline as FBI assumes control






