Photo: Primakov / Shutterstock.com
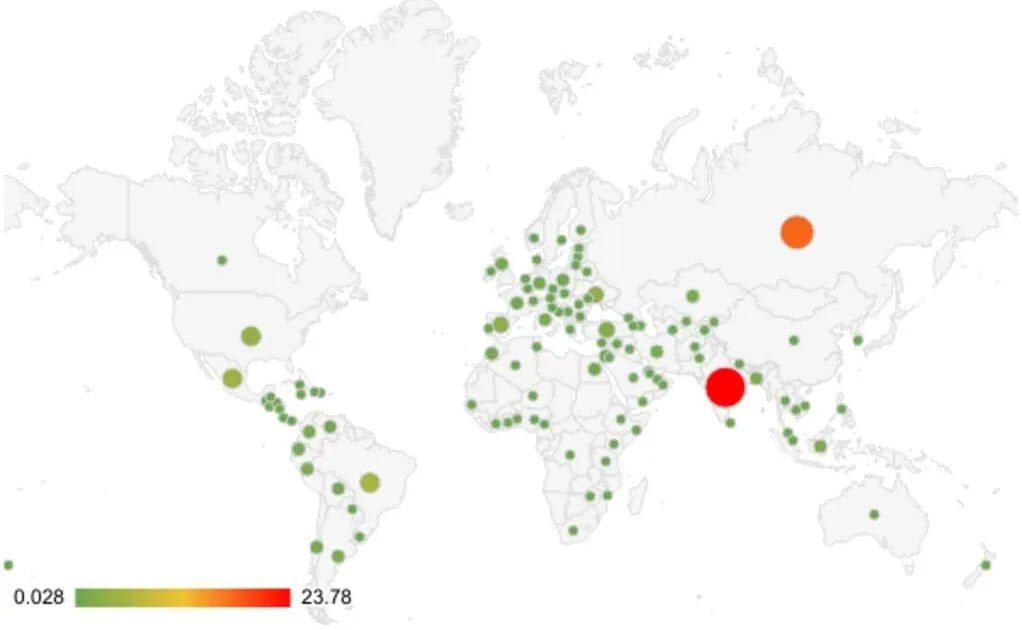
A sophisticated cybercriminal campaign is wreaking havoc across Android devices worldwide, leveraging thousands of Telegram bots to disseminate SMS-stealing malware in 113 countries, including India, Russia, Mexico, the U.S., and Brazil, among others. This operation has been running since February 2022, creating at least 107,000 distinct malware samples.
According to researchers, the primary objective of cybercriminals appears to be financial gain, exploiting infected devices for authentication and anonymisation purposes.
The malware, designed to exfiltrate one-time passwords (OTP) from SMS messages, is disseminated through two primary methods. The first involves malvertising, where victims are directed to counterfeit pages imitating Google Play.
These pages display exaggerated download figures and aim to deceive users into installing malicious software.
The second method involves Telegram bots, which promise users access to pirated Android applications. To receive the APK file, victims must provide their phone numbers. This information is then used to generate a customised APK, facilitating targeted tracking and enabling future attacks.
“Upon installation, the malicious application requests permission to read the SMS message. This high-risk permission on Android grants extensive access to sensitive personal data. While legitimate applications may require SMS permissions for specific, well-defined functions, this particular app’s request is likely unauthorised and intended to exfiltrate the victim’s private text message communications,” researchers explain.

Researchers estimate that this massive campaign employs approximately 2,600 Telegram bots to promote malicious APKs. These bots are managed through 13 command and control (C2) servers.
“Once the victim’s device has registered with its configured C&C server, the malware can begin stealing the victim’s personal information, including but not limited to SMS messages and phone details. This information is then forwarded from the victim’s device to its configured C&C server,” researchers wrote.
The stolen SMS messages are sent to an API endpoint linked to the ‘fastsms.su’ website, which offers virtual phone numbers for anonymity and authentication purposes. This data suggests that the infected devices might be used by this service without the victim’s knowledge.

The malware’s capability to capture OTPs poses a severe risk, as it can facilitate unauthorised access to online accounts and services, potentially leading to financial losses and legal complications for the victims.
The illicit access to virtual phone numbers could result in victims incurring unauthorised charges or being lined up for criminal activities traced back to their devices.
Researchers have urged users and enterprises to install robust mobile security measures and avoid clicking on unknown links. Furthermore, installing apps from trusted sources lessens the risk of malware and associated activities.
In the News: Amazon held responsible for recalling 400,000 “dangerous” products






