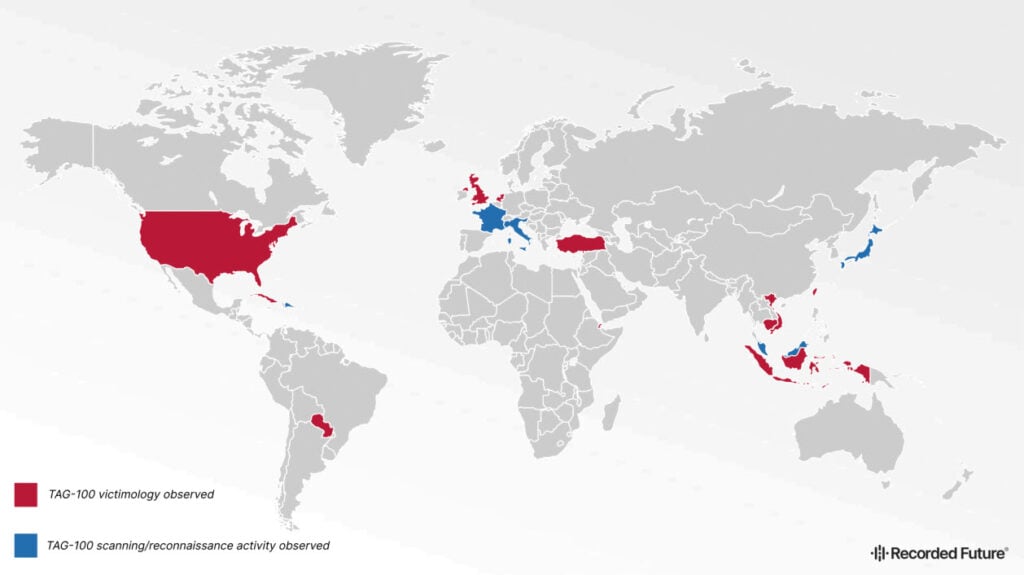
A cyber-espionage campaign, dubbed TAG-100, is actively targeting high-profile government, intergovernmental, and private sector organisations in the United States, the United Kingdom, Cambodia, Djibouti, the Dominican Republic, Fiji, Indonesia, Netherlands, Taiwan, and Vietnam, using open-source remote access tools.
Moreover, researchers discovered TAG-100 scanning/reconnaissance activities in France, Italy, Japan, Cuba and Malaysia. The campaign targeted Cuban embassies in Bolivia, France, and the United States. They have also revealed that the campaign has infiltrated various entities, from diplomatic missions to industry trade associations and semiconductor supply chains in Taiwan.
Here’s a list of organisations affected by the cyberattack:
- Government and diplomatic entities: Ministries of Foreign Affairs across Southeast Asia, South America, and the Caribbean, including embassies.
- Private sector: Semiconductor companies, financial trade associations, and industry trade groups.
- Non-profit and religious organisations: Numerous organisations in the US and Taiwan.
“TAG-100’s arsenal includes the Go-based backdoor Pantegana, which provides multi-platform support (Windows, Linux, OSX) and leverages HTTPS for command-and-control (C2) communications,” researchers note.
The group’s operation also involves:
- Publicly available exploits: For vulnerabilities in popular internet-facing appliances like Citrix, NetScaler, F5 BIG-IP, Zimbra Collaboration Suite, Microsoft Exchange, SonicWall, Cisco ASA, and Fortinet FortiGate products.
- Open-source post-exploitation frameworks: Utilising tools like SparkRAT, LESLIELOADER, and Cobalt Strike, alongside custom implementations for enhanced stealth and effectiveness.
TAG-100 conducts extensive reconnaissance on internet-facing devices, which are often neglected in terms of security. This includes devices with limited visibility and logging capabilities, making them attractive targets for cyberespionage.
In March 2024, the campaign targeted Citrix NetScaler and F5 BIG-IP devices and Outlook Web App login portals globally. In most cases, these devices overlapped, leading them to communicate with the C2 servers.
Researchers observed that beginning on April 16, 2024, TAG-100 began targeting Palo Alto Networks GlobalProduct appliances, exploiting the CVE-2024-3400 remote code execution flaw. Other than that, the campaign also exploited the Zimbra Collaboration Suite vulnerability CVE-2019-9621.
While researchers refrained from definitive attribution, TAG-100’s targeting patterns and techniques suggest an espionage motive, potentially aligning with state-sponsored. The group’s focus on intergovernmental, diplomatic, and religious entities mirrors historical campaigns attributed to Chinese state-sponsored groups.

However, using open-source tools complicates direct attribution, as less sophisticated threat actors may also employ these tools.
Researchers have urged organisations to prioritise patching perimeter devices based on intelligence-led assessments of exploit availability and to focus on regular audits and reducing attack surfaces.
“The exploitation of vulnerable internet-facing devices by TAG-100 is particularly concerning due to the limited visibility and logging capabilities of these devices. This reduces the risk of detection post-exploitation and exposes organisations to operational downtime, reputational damage, and regulatory fines,” researchers concluded. ” The use of open-source tools also allows state-sponsored threat actors to outsource cyber operations to less capable groups, increasing the intensity and frequency of attacks on enterprise networks.”
Last week, reports came out that a Chinese threat actor, Simishing Triad, was targeting Indian users via India Post phishing lures. In June, another China-based threat actor, RedJuliett, was found to be targeting ten countries, including Taiwan, Hong Kong, the Philippines, and the United States.
In the same month, reports surfaced indicating that a massive Chinese-run scam operation in Myanmar was dismantled due to international pressure, domestic outrage, and geopolitical realignments.
In the News: Rite Aid data breach exposes 2.2 million customers’ information






