A newly discovered campaign by the East Asian APT group UTG-Q-010 targets cryptocurrency enthusiasts with precision-engineered phishing attacks. The group, active since late 2022, has rapidly evolved its tactics, deploying advanced malware, PupyRAT, and exploiting legitimate Windows processes to breach defences.
UTG-Q-010 has established a reputation for its meticulous approach to phishing campaigns. Earlier attacks by the group targeted HR departments within the gaming industry by posing as major gaming companies looking to recruit developers.
However, the hacking group has turned its attention to the rapidly expanding digital currency market over the past few months. This strategic pivot reflects the group’s ability to identify and capitalise on new financial opportunities when they arise.
“CRIL recently came across samples related to UTG-Q-010 targeting cryptocurrency enthusiasts by employing a sophisticated phishing attack involving a zip file containing a malicious LNK file,” researchers note.
Their most recent operations exploit the excitement of cryptocurrency-related events, revealing a sophisticated grasp of human psychology. By tapping into the hype and promise associated with digital assets, the group has devised methods to compromise even typically vigilant targets.

According to researchers, the recent campaign attributed to UTG-Q-010 involves carefully orchestrated phishing attacks targeting cryptocurrency enthusiasts. The group employs a sophisticated phishing technique involving a malicious LNK file disguised as an invitation to a non-existent cryptocurrency event named ‘Michellin Night: Coin Circle Friendship Feast.’
This seemingly legitimate invitation was hosted on a suspicious URL: ‘hxxp://malaithai.co/MichelinNight[.]zip,’ where the ZIP file ‘MichelinNight.zip’ housed the malicious LNK file ‘MichelinNight.Ink.’
Upon execution, this LNK file initiates a series of commands that manipulate legitimate Windows processes to deliver a malicious payload. The initial command copies the legitimate Windows Error Reporting tool (WerFault.exe) to a temporary directory and then employs PowerShell in hidden mode to execute a carefully crafted script.
The PowerShell script executed by the LNK file is a prime example of UTG-Q-010’s technical prowess. It begins by searching for LNK files in the current directory that match a specific size, a technique used to identify the malicious LNK file itself.
Once identified, the script reads the file’s content as a byte array and decrypts it using a bitwise XOR operation with a key embedded within the script. The decrypted content is then saved as a DLL file named faultrep.dll in the Temp directory.
The DLL file serves as a malicious loader responsible for executing the attack’s final payload. However, before doing so, the script employs advanced evasion techniques to ensure it is not being analysed in a controlled environment.
The loader checks the infected system’s username against a list of known usernames associated with popular sandbox environments.
Additionally, it examines the system’s MAC addresses to identify those commonly associated with virtual machines, and it scans for artifacts related to virtualisation tools such as VMware and VirtualBox.
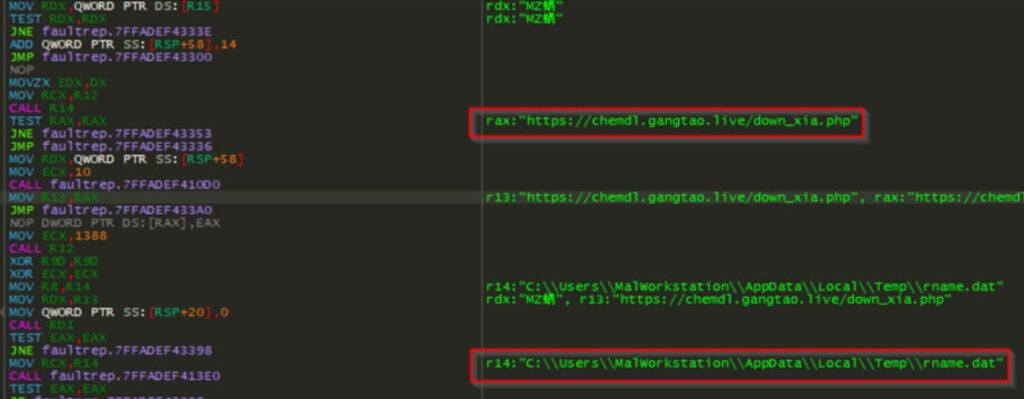
The loader only continues operating after ensuring it isn’t running in a sandbox or virtualised environment. To do this, it checks if the compromised system has an active internet connection by trying to access the Chinese search engine Baidu at https://www.baidu.com. Once this connection is confirmed, the loader fetches an encrypted payload from hxxps://chemdl.gangtao[.]live/down_xia.php and saves it temporarily as ‘rname.dat’ in the Temp directory.
Researchers have observed that the final step involves decrypting this payload, revealing the PupyRAT—a versatile and powerful Remote Access Trojan (RAT) used for post-exploitation activities.

This trojan operates almost entirely in memory, leaving minimal traces on the compromised system. Its in-memory execution model and its ability to inject processes reflectively and execute remote Python code make it a formidable tool for maintaining long-term control over compromised systems.
“Pupy is a versatile, cross-platform Remote Access Trojan (RAT) and post-exploitation tool, primarily developed in Python. It operates stealthily with an in-memory execution model, leaving minimal traces on host systems. Pupy supports multiple communication means of transport, enabling adaptability to diverse network environments and evasion of detection,” researchers cautioned.
Researchers have urged organisations to deploy advanced email filtering to block phishing emails, educate their employees, set up detection rules to identify unusual activities and install endpoint detection and response (EDR) solutions.
In the News: TRAI rolls out tougher rules to combat spam calls in India






