A critical remote code execution vulnerability, namely CVE-2022-22954, in VMware’s Workspace One Access program, also called VMware Identity Manager, is being actively exploited by advanced hackers. The issue has already been patched roughly 20 days ago, alongwith two other RCEs.
The two additional RCEs — CVE-2022-22957 and CVE-2022-22958 — also impact VMware Identity Manager, VMware vRealize Automation, VMware Cloud Foundation and vRealize Suite Lifecycle Manager. A patch for the initial vulnerability was issued on April 6, and by April 11, a proof of concept exploit for the attack was publicly available. By April 13, security researchers identified exploits running in the wild.
Researchers at Morphisec have seen exploitation attempts from several advanced persistent threat actors, most notably from an Iranian hacking group called Rocket Kitten, tracked as APT35.
In the News: Elon Musk buys Twitter for $44 billion
Attacks linked to a shady hosting firm
The attack can be used to deploy anything from ransomware to crypto miners on the target servers. What’s perhaps more dangerous is the fact that researchers found exploits attempting to install reverse HTTPS backdoors, mostly Cobalt Strike, Metasploit or Core Impact beacons. Additionally, when run with privileged access, these attacks may also be able to bypass antivirus protection and endpoint detection and response.
The attack starts by running a PowerShell command on Identity Manager, launching a stager for further work. Initial access is gained by exploiting CVE-2022-22954, which doesn’t require administrator access to the target server while also having a publicly available proof of concept exploit.
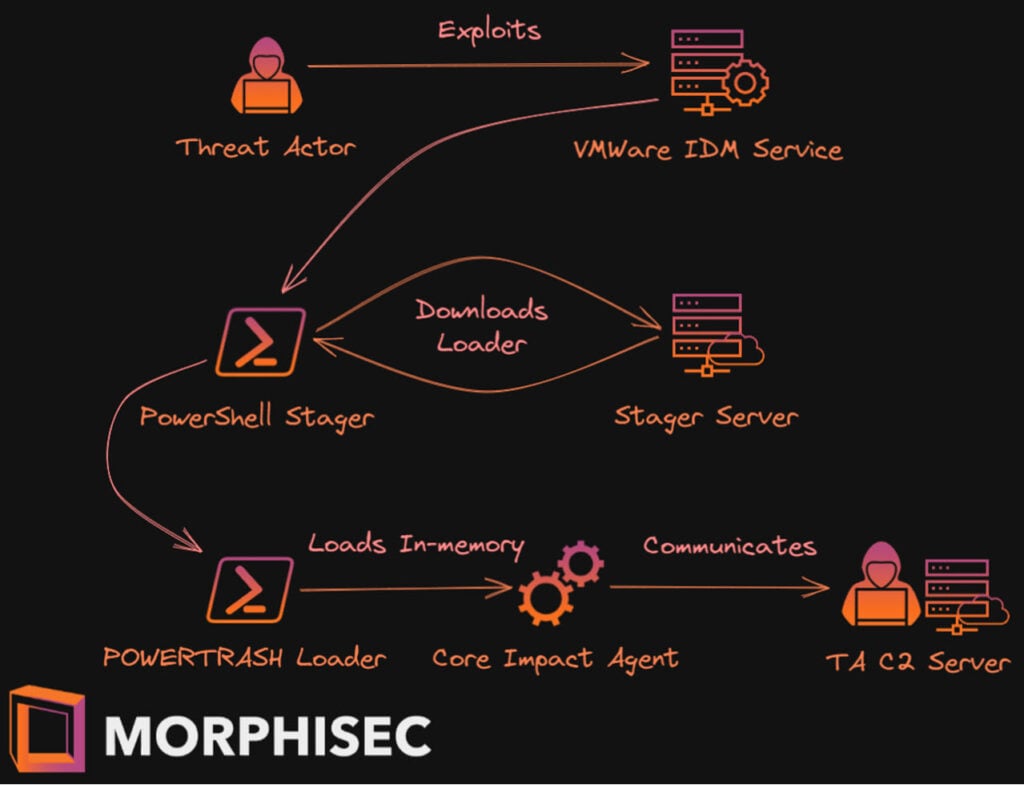
Once the stager is launched, it can fetch the PowerTrash loader from the command and control server in an encrypted form and launches a Cobalt Strike, Metasploit or Core Impact service in the memory.
Morphisec researchers obtained the stager server’s C2 address, the Core Impact client’s version and the 256-bit encryption key used for communication between the stager and the C2 server. The operation has been linked to a person called Ivan Neculity.
The Huckster’s fraud database has an entry under that name stating that Ivan is a Russian citizen and lists corporate entities in Moldova, Russia and the UK including a hosting firm which supports a number of illegal websites in addition to spam and phishing campaigns.
In the News: $1 million worth of BAYC NFTs stolen in Instagram phishing hack






