Cybersecurity researchers have discovered a novel phishing campaign that targets job seekers with recruiting and job-based messages and delivers a Windows-based backdoor named WarmCookie. That said, the backdoor only seems to be the first stage of the attacks, as researchers report that it’s only an initial tool used to scout victim networks and deliver additional payloads if required.
Elastic Security Labs discovered the campaign, noting that WarmCookie can also fingerprint and capture screenshots of the victim machine and deliver payloads. The campaign, dubbed REF6127, is also rapidly expanding, with threat actors developing new domains and infrastructure weekly to support their enterprise.
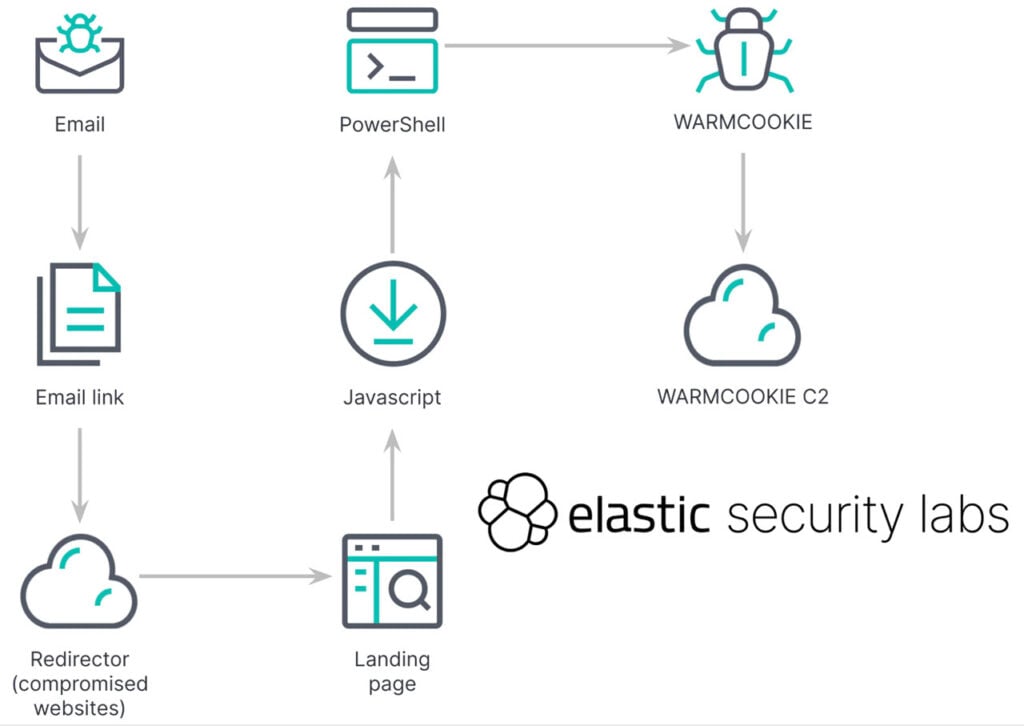
REF6127 targets individuals by their names and current employers, luring them to pursue new, bogus job opportunities by clicking a link to an internal system to view a job description. Once clicked, the targeted user lands on a legitimate-looking webpage specifically crafted for them. Upon arrival, they’re asked to download a document by solving a CAPTCHA challenge.
Once the CAPTCHA is solved, a hidden JavaScript file is downloaded, which runs a Windows PowerShell script. This script, in turn, abuses the Background Intelligent Transfer Service (BITS) to download WarmCookie and run it as a DLL file.
The threat actor behind the scheme is pushing to target different recruiting firms and combinations with keywords related to the job search industry. Additionally, they further distance themselves from the campaign by using compromised infrastructure to host the initial phishing URL, redirecting to different landing pages. After each campaign runs, once a particular domain earns a bad reputation, the threat actor generates a new domain to progress the campaign further.

The initially delivered WarmCookie payload is a two-stage DLL-type backdoor. The first stage involves moving the malicious DLL file from a temporary directory with a random name to the ProgramData folder found in the Windows installation drive.
Once the malware has copied itself, it sets persistence using COM with the Windows Task Scheduler, running the DLL with administrative privileges. From this point onwards, the backdoor fingerprints the machines by capturing the volume serial number, DNS domain, computer name, and user name.
It then makes its first outbound request to the Command and Control (C2) infrastructure to await further commands, communicating over HTTP with a hardcoded IP address. The backdoor offers seven command handlers to record victim information, take screenshots, read or write files on the target PC, launch additional malicious payloads, or even delete scheduled task persistence.
Elastic Labs will continue to monitor the threat, believing it to be a “formidable threat,” and recommends that the security industry do the same. They note that there’s scope for malware development and that further updates to the backdoor may improve its capabilities while making it harder to detect.
In the News: Waymo issues recall after robocar collides with telephone pole






