A rather famous Scottish brewery and pub chain Brewdog has irreversibly exposed the details of over 200,000 of its shareholders and customers, according to PenTestPartners. The exposure lasted for around 18 months and stemmed from the company’s mobile app.
The flaw was discovered all the way back in March 2020 in version 2.5.5 of the app. The Brewdog team was immediately informed of the issue but failed to fix it in the next four updates. The issue was fixed in version 2.5.13 released on September 27, 2021, and even then Brewdog failed to report any vulnerabilities in the update notes.
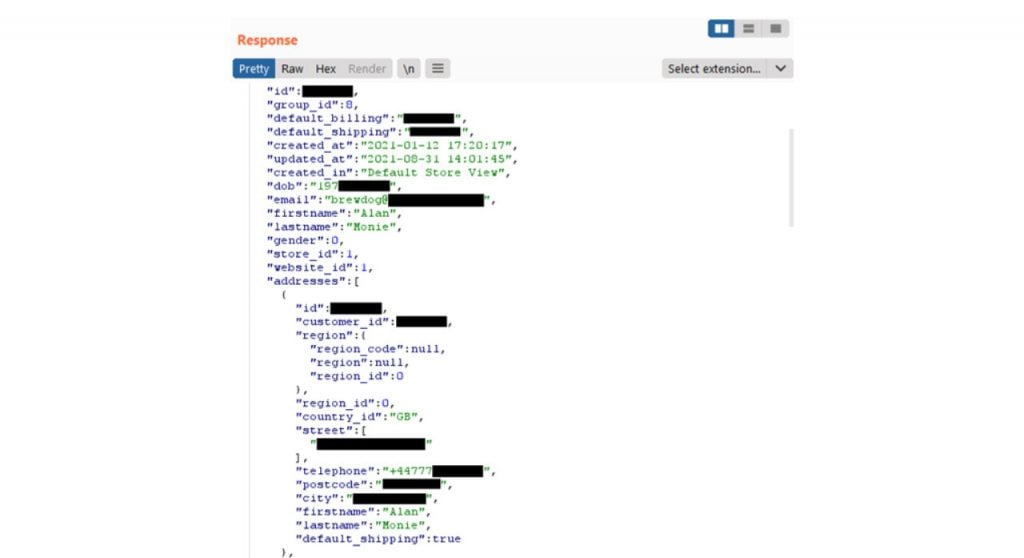
The problem lies in the app’s API or, more specifically, the way the API deals with its token-based authentication system. Instead of being transmitted to the app following a successful user authentication attempt, these tokens were hard-coded. This allowed anyone to append any customer ID to the end of the API’s endpoint URL and access all information about that particular customer.
In the News: Twitch breach results in 125GB worth of source code leak
Free beers for hackers
This is more of a blunder from Brewdog’s app developers rather than a security flaw. An attacker can easily access the following information using this method.
- Name
- Date of Birth
- Registered Email
- Gender
- Previously used delivery addresses
- Phone number
- Number of shares held
- Shareholder number
- Bar discount amount
- Bar discount ID
- Number of referrals
- Type of beer previously purchased
The customer IDs that need to be appended to the API’s endpoint URL to fetch this information aren’t sequential, but an attacker could just use a combination of random numbers and brute force API requests to fetch any user’s data.
Sensitive information aside, this flaw can also get an attacker unlimited free beer. Brewdog has a scheme that offers free beer to customers three days before or after their birthday. In theory, an attacker can find a customer ID with the date they want, use the bar discount ID fetched from the API to generate a barcode and get free beer whenever they want.
The researcher has reported that Brewdog downplayed the importance of the findings and failed to address the issue promptly, going as far as to deny outright seeing any evidence of a data breach repeatedly. Brewdog hasn’t informed its shareholders and customers of the possibility of their data being breached either.
The way this exploit works won’t leave any signs to look for in the first place, apart from possibly a large number of API requests which could just be any regular person using the Brewdog app as well.
In the News: NFT ‘fantasy startup investing’ platform shuts down citing legal trouble






