A novel ransomware strain dubbed ‘Cactus’ has been found to be exploiting vulnerabilities in Fortinet VPN devices to gain initial access to corporate or other large-scale networks. While the ransomware is pretty standard it its operation, research has shown that it encrypts itself as an evasion technique against antivirus programs.
The operation has been active since at least March 2023 and was discovered by researchers at Kroll, a corporate investigation and risk consulting firm. According to researchers, once initial access is gained by exploiting vulnerabilities in Fortinet’s VPN devices, the hacker uses a batch script to fetch the encryptor’s binary executable using 7-Zip. Then, the original ZIP archive is removed and the binary file runs with a specific flag allowing it to execute as intended.
There are three main modes of execution here, all controlled via different command line flags. The first two flags, namely setup (-s) and read configuration (-r) let the hackers set up persistence and store data in C:\ProgramData\ntuser.dat file which is later read by the encryptor using running with the -r flag.
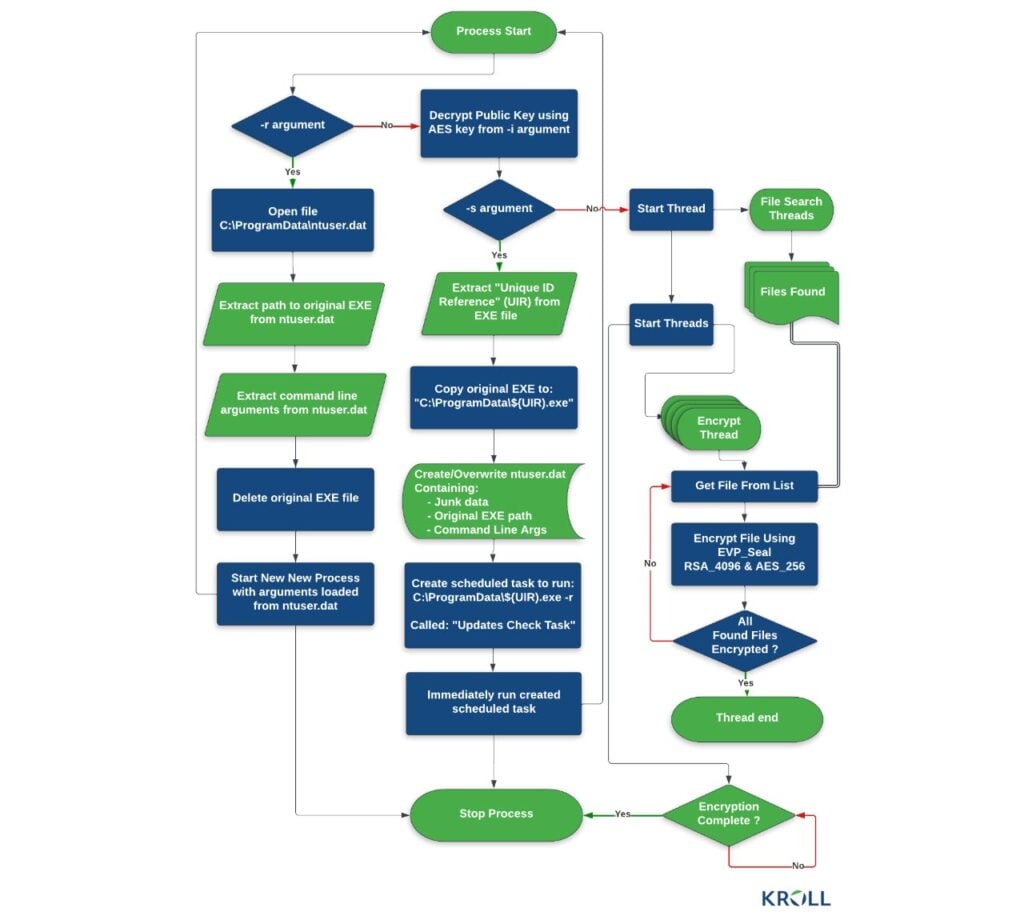
Finally, the third execution mode is run. This encryption mode (-i) uses a unique AES key known only to the attackers and encrypts everything on the system. It’s also required to decrypt the ransomware’s configuration file and the public RSA key required to encrypt files on the compromised system.
By encrypting its own configuration file, the ransomware essentially encrypts itself making it difficult for antivirus and network monitoring tools to detect any malicious activity. When the binary is run with the right AES key alongside the -i flag, the ransomware unlocks its configuration information and starts searching for files to start a multi-thread encryption process.
Speaking of the encryption process, Cactus has two ways of encrypting files. It also uses multiple extensions for targeted files based on their processing state. Ransomware expert Michael Gillespie told BleepingComputer that the ransomware uses the .CTSo extension when preparing files for encryption and switches to .CTS1 once encryption is complete. For faster encryption, the ransomware also as a “quick mode” which is essentially a faster but weaker encryption run. Additionally, the number at the end of the .CTS extension can vary.
Cactus also makes use of several legitimate programs to breach networks and target machines. The ransomware uses SoftPerfect Network Scanner (netscan) to look for targets on the networks combined with PowerShell commands for more in-depth recon. Researchers also discovered a modified variant of PSnmap, an open-source tool which is the Windows equivalent of Linux’s nmap network scanner.

Multiple other legitimate tools like Splashtop, Anydesk, Superops RMM and Chisel were also used in the attacks, alongside the Cobalt Strike backdoor. Once the attackers get elevated privileges on a machine, a batch script also uninstalls the most commonly used antivirus programs that might be present on the target machines.
At the moment, the ransomware group doesn’t have a victim site and there’s no public information about any ransoms that they may have demanded from their victims. That said, ransom notes have been found on compromised machines claiming that the stolen data will be published unless a ransom is paid.
In the News: Hackers stole WD customer data in March attack




