Threat actors use the Discord chat platform to distribute Lumma Stealer, a malware specialising in information stealing.
Researchers from Trend Micro analysed the stealer and found out that the threat actors are exploiting the Content Delivery Network (CDN) to host and distribute Lumma Stealer while also utilising the platform’s Application Programming Interface (API) to create malicious bots that control the malware and pilfer data to private Discord servers and channels.
Lumma Stealer, coded in the C programming language and designed to filch user credentials, is the latest family distributed via Discord’s CDN. This malware was initially spotted in August 2022, with reports emerging earlier this year regarding Lumma Stealer operators targeting YouTube users through spear-phishing emails.
The researchers also discovered that the Lumma Stealer’s starting price is around $250 per month in underground forums, with the highest cost being $20,000 per month.
Lumma Stealer: Tactics explained
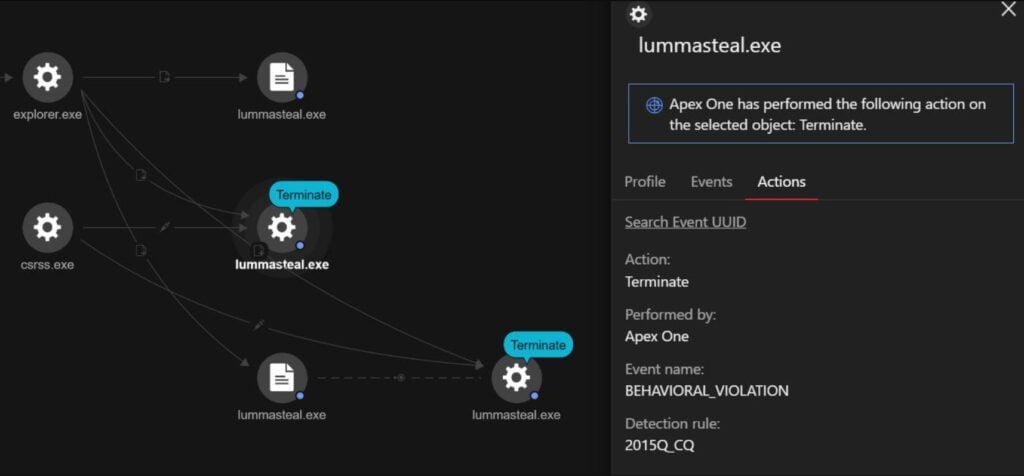
The tactics employed by Lumma Stealer operators are characterised by using random Discord accounts to send direct messages to victims. Malicious actors also exploited compromised Discord accounts to target the connections of the compromised accounts.
The attackers first engaged the victims by offering $10 or a Discord Nitro boost in exchange for help with the purported project. Nitro boosts are part of Discord’s subscription-based server-boosting, enticing users with special perks on specific servers. This offer serves as bait to entice victims into playing a game and providing a review, which the attackers claim will take only a few minutes. Should the victim consent, they are prompted to download a file.
During the investigation, a victim received the Discord message via Google Chrome. Upon clicking the malicious link, multiple downloads of the file ‘4_iMagicInventory_1_2_s.exe’ occurred, containing the Lumma Stealer malware.
When executed, this file is connected to the malicious domain ‘gapi-node[.]io’ and attempts to pilfer cryptocurrency wallets and browser data.
Growing capabilities of Lumma Stealer
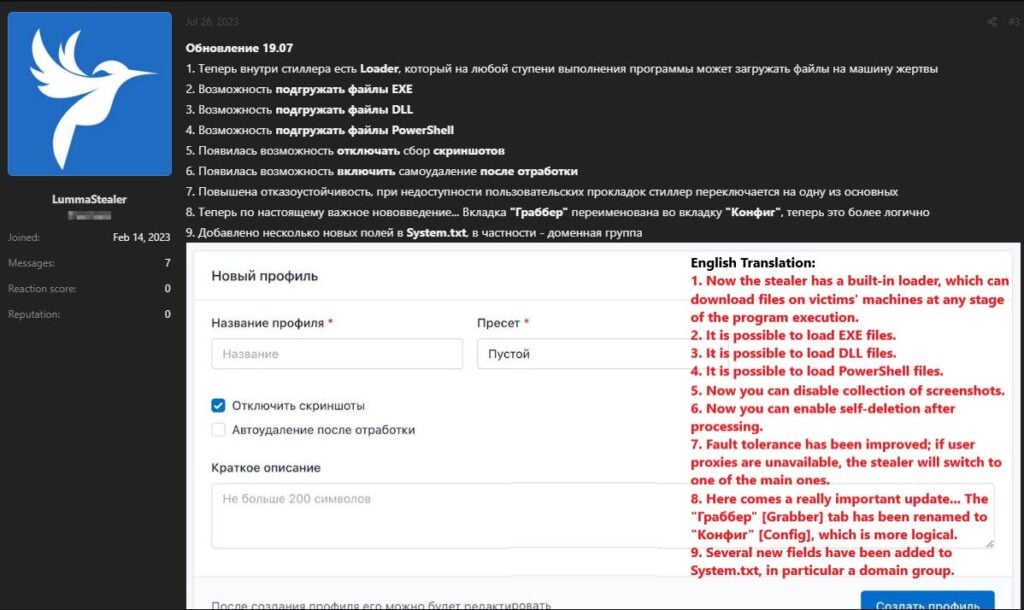
Threat actors associated with Lumma Stealer have boasted on underground forums that the malware can now load other files, which often leads to installing additional malware.
Furthermore, they have announced that Lumma Stealer can now employ artificial intelligence and deep learning to detect and filter out bots. It is presumed that in his context, bots refer to security researchers, analysis environments, and emulators.
To mitigate the risks of this malware, researchers have requested users to avoid opening direct messages on any platform if it’s from an unknown entity, use any reputable third-party antivirus software, and organisations should provide security training to employees.
In the News: India to enforce WhatsApp traceability law to counter deepfakes




